The Corellium Resource Library
The latest articles and news on mobile app security testing, IoT and research from Corellium and community contributors.

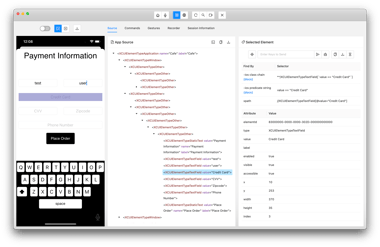
Corellium announces unparalleled support for iOS 26 and full iPhone 17 device support, dynamic mobile application risk scoring, and several other new capabilities as well as expanded global support for Corellium virtual servers.
Load More
Subscribe to Stay Connected
Keep up to date with emails for the latest product news and technical articles.






































































































.png?length=380&name=Corellium+Arm_Blog_Post_Image_v1%20(1).png)