nekoJB Jailbreak Scam? Investigating the iOS 18.7 Fake Jailbreak Trap
A new version of “nekoJB jailbreak” is circulating online, claiming to support iOS 18.7 through iOS 26. But is this the real deal, or just another iPhone jailbreak scam targeting iOS users?
Using a Corellium iPhone 16e running iOS 18.5 and Safari Web Inspector on macOS 15.6, our research team analyzed every step of the so-called jailbreak. What we found wasn’t a jailbreak at all—but a well-disguised scam engineered to harvest trust, traffic, and possibly credentials.
How Jailbreaking Went Underground
Jailbreaking is the process of gaining local privilege escalation (privesc) on a device, typically by exploiting the kernel or lower-level hardware such as the bootrom. This bypasses Apple’s security mitigations and facilitates elevated system privileges including unsigned code execution, reading/writing kernel memory, and more.
iOS jailbreaking began not long after the first iPhone was released, and for over a decade, it played a major role in shaping both the platform and the broader mobile security landscape. Today, however, the scene looks very different.
After the checkra1n and palera1n era, there was a steep drop-off in publicly available jailbreaks. The slowdown wasn’t just technical—it was economic. Apple’s security bounty program, its more hardened security posture, and the rise of private exploit markets all shifted the calculus. Holding onto a zero-day is now far more profitable than releasing a public tool.
Put simply: jailbreaking became harder, and the incentives to keep vulnerabilities private grew stronger.
Despite that decline, the jailbreaking community had a lasting influence. Many iOS features we now take for granted—custom UI tweaks, AirDrop (AirBlue), and better file management (iFile) originated in jailbreak tools long before Apple adopted them.
The Original nekoJB
On December 27, 2023, a jailbreak called nekoJB was released for iOS versions 15 through 15.8 by a developer known as HAHALOSAH, according to the Apple Wiki. nekoJB is a fork of the Dopamine jailbreak and leverages several exploits, including a vulnerability in Apple’s DriverKit that enables arbitrary kernel read/write primitives.
It follows a traditional installation method: an IPA file is sideloaded onto the iPhone, and the exploit is executed locally on the device.
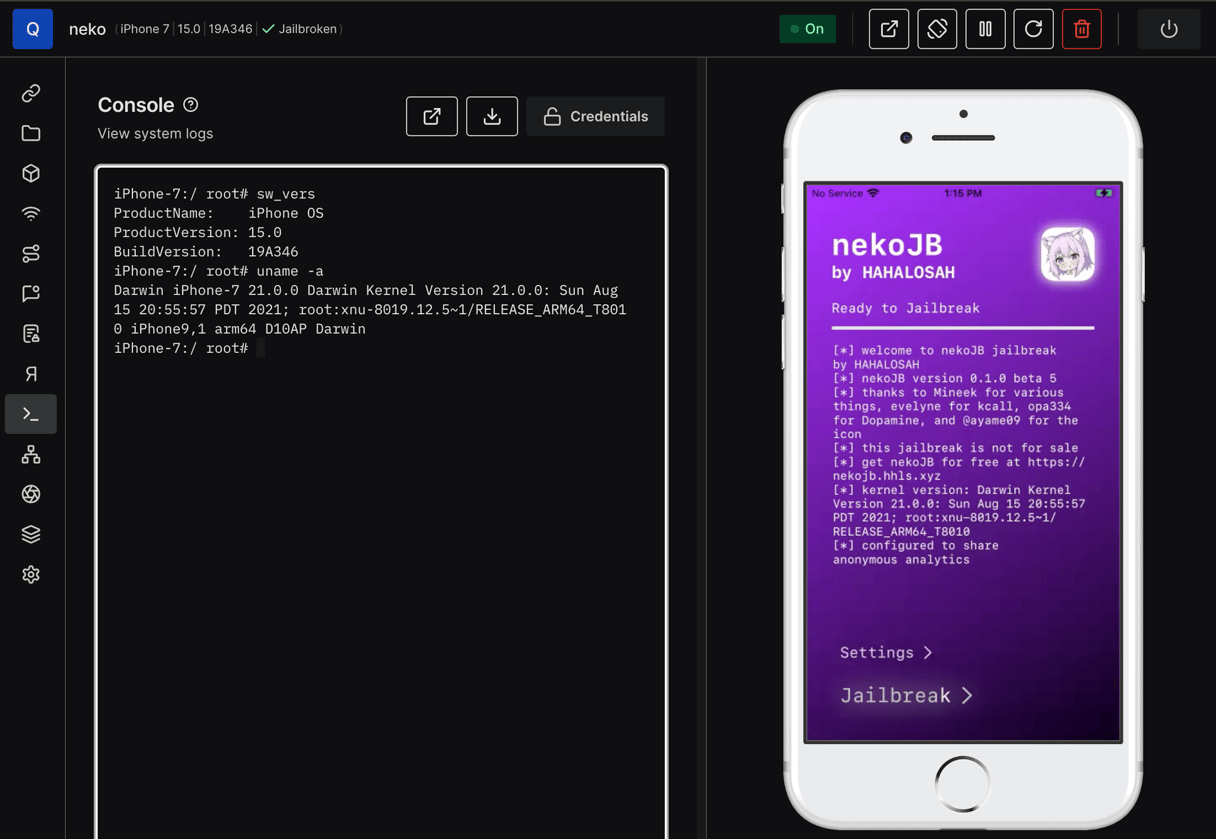
Figure 1-1 shows the IPA installed on a Corellium Virtual Machine (VM).
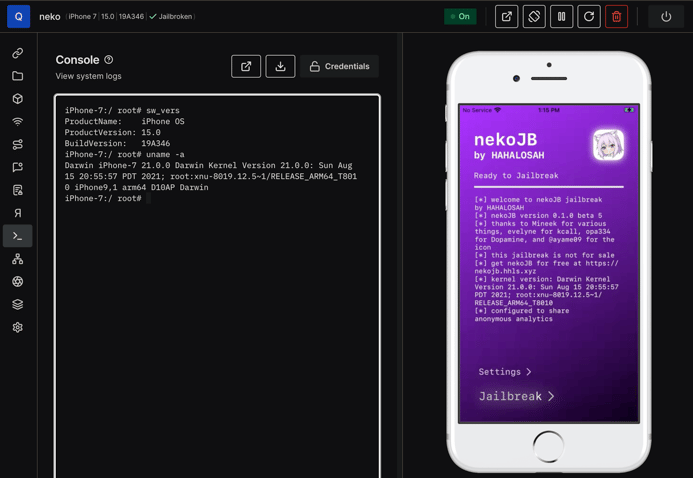
Figure 1-1
The nekoJB Scam: Bold Jailbreak Claims, Zero Proof
A newer version of nekoJB is currently making the rounds in the iOS jailbreak community. While most call it a hoax, others are still downloading it and crossing their fingers for the next big breakthrough—or at least something that looks real.
The Corellium Labs team installed and dissected this online jailbreak, revealing its true nature.
Inside Corellium’s Test Environment
We used a Corellium instance to install and interact with nekoJB online. We also used Safari, Apple’s native browser on an external iDevice for inspecting web pages with the Web Inspector utility and the iOS web agent enabled:
- Corellium Instance: iPhone 16e - iOS 18.5
- Local Machine: M2 Macbook - macOS 15.6
This virtual environment is the gold standard for mobile app security testing and research. Want to try it for yourself? Request a free trial of Corellium today!
Anatomy of nekoJB Online
Navigating to the nekoJB Online website from the Corellium Virtual Platform, we are directed to a download site, which downloads a.mobileconfig profile for the user to install. This profile contains a web clip and a root certificate authority, which we'll touch on later.
Web clips are device management utilities, commonly used by Mobile Device Management (MDM) to conveniently redirect a user to an embedded link or URL. In this case the profile’s web clip acts as a shortcut to a third-party app store zJailbreak. It’s known for hosting a collection of jailbreaks, custom themes, and third-party apps. In the zJailbreak web clip, the neko Online Jailbreak “app” is listed under the premium tier, requiring the user to make a donation in order to install the “app.”
Instead, if we use a mac to navigate to the web clip URL embedded in the .mobileconfig profile on Safari we can utilize the web inspector to inspect the JavaScript used for the web page.
In Figure 1-2 we can see the JavaScript used in the zJailbreak web page, which reveals the download link for the .mobileconfig profile that provides premium tier access in the zJailbreak app store.
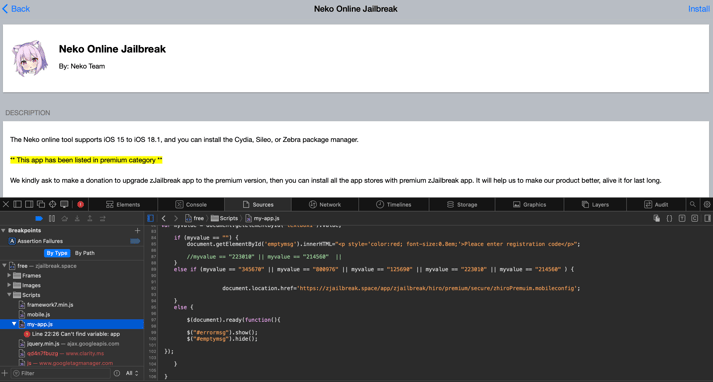
Figure 1-2
Now that we have the URL for the new premium .mobileconfig profile, we copy and paste that URL into Safari on the Corellium Virtual Machine which allows us to download and install the zJailbreak web clip with premium access. Navigating back to neko Online Jailbreak in the app store, we’ll now be able to install the “app.”
The Fake “App” Experience
After installing the nekoJB Online “app”, we can see that this is another.mobileconfig profile that contains a web clip redirecting the user to https://nekojb.com/source/nekojb. On this web page we can see that it bears almost an identical resemblance to the nekoJB IPA (Figure 1-3). While the interface mimics the real nekoJB jailbreak, it's a facade. Behind the scenes, nekoJB Online functions more like a credential harvesting jailbreak trap than a legitimate tool.

Figure 1-3
A few things to make note of right off the bat: the jailbreak menu displays misspelled words, line wrapping issues, and an inaccurate kernel version. Digging into the web page's source code using the same web inspector method, we can see that the kernel versioning is all HTML text (Figure 1-4), which begins to raise serious concerns — as having an accurate kernel version is important when you're trying to exploit it.
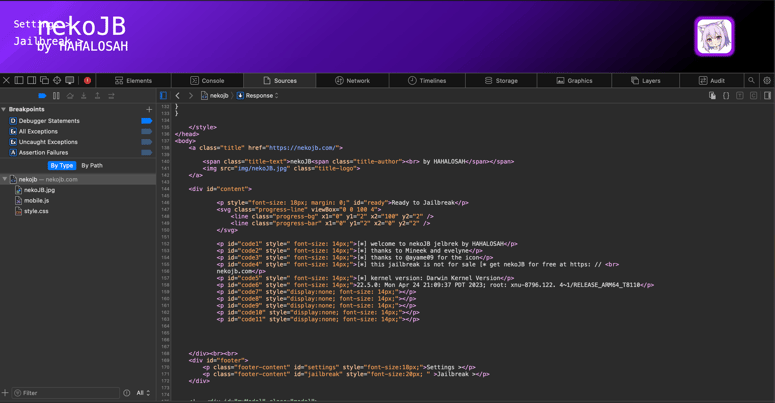
Figure 1-4
The Synthetic Exploit
As highlighted earlier, a jailbreak must leverage vulnerabilities found in the software and/or hardware to escalate privileges on the device. With that in mind, let's start our iOS 18.5 jailbreak. Almost immediately, we can see duplicated chunks of text being displayed roughly every couple of seconds and a .mobileconfig profile that's downloaded at the end.
To investigate this further, let's take a look at the source code from https://nekojb.com/source/nekojb.
Roughly halfway down we can see HTML text (Figure 1-5), this time containing random static kernel offsets, assembly instructions, function calls, typos, and at the very end we see yet another .mobileconfig profile being downloaded. This time the profile contains a web clip with a URL to https://nekojb.com/source/nekojb/nekoutil.
Based on the evaluated web page source code, It’s obvious here that the developer’s intentions are to deceive the user by making them believe that their device has been exploited and is now jailbroken.
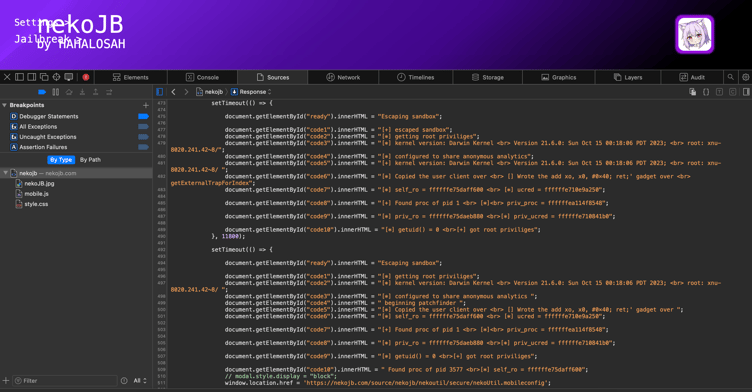
Figure 1-5
The Bigger Threat: iOS Jailbreak Scams and Credential Harvesting
Taking a look at the new web clip, nekoUtil, we can see a menu with 3 sections: Package Managers, Additional Software, and Quick Actions (Figure 1-6). Instead of applications, the package managers are all .mobileconfig profiles:
- zebra.mobileconfig
- sileo2.mobileconfignfig
- cydianew.mobileconfig
Authentic third-party package managers such as Cydia would install applications by installing the .ipa directly onto the device, which is possible because security mitigations including code signing and sandboxing are not strictly enforced on jailbroken devices. The package managers provided through nekoUtil cannot install applications onto the device, so they rely on web clips from .mobileconfig profiles.
Package managers aside, the Additional Software and Quick Action sections of nekoUtil contain several icons all sharing the same “high quality” code shown in Figure 1-7.
What’s interesting is that if the device's version of iOS is less than or equal to 18.0 the icon will display an alert stating that this feature is not supported; if the version of iOS is 18.1 then the same alert occurs. However, if the version is anything greater than iOS 18.1, then the same alert is still displayed. In short, every option did nothing. Given how nekoJB Online targets both iOS and Android users with deceptive jailbreak claims, it's important to recognize these scams early, whether it's a nekojb scam iOS tool or a nekojb scam Android variant.

 Figure 1-6 Figure 1-7
Figure 1-6 Figure 1-7
nekojb Jailbreak Analysis Summary
After downloading, installing, and dissecting nekoJB Online, it’s clear that there is no jailbreak. Instead, the profiles installed onto the user’s device contain root certificates, which allow for the developer, or operator, to act as an intermediary for all internet traffic emitting from or transmitting to the device.
The root certificates are embedded into each and every profile installed onto the device, allowing for network traffic monitoring, download hijacking, network traffic manipulation, and credential harvesting.
nekoJB Online’s usage of web clips also serves as an illusion to the device being in a jailbroken state, going so far as to replicate well-known package managers to perhaps provide a sense of familiarity and legitimacy. The Santander icon under the Additional Software section of nekoUtil (Figure 1-6) also raises curiosity.
Santander is a third-party file manager where users can store and organize their files. Replicating this app’s functionality would allow for primitives such as exfiltrating stored files.
From these conclusive results, it’s safe to say this is not a jailbreak and should not be treated as one. Be sure to exercise extreme caution when downloading software from unverified sources, and pay attention to red flags such as jailbreaking fees, root certificates, and promises that sound too good to be true.
Corellium’s Lab analysis shows how fake jailbreaks can be weaponized for surveillance and procurement of sensitive user data, and why careful verification (and safe testing environments) matter more than ever.
Why Corellium Matters More Now Than Ever
nekoJB Online isn’t a jailbreak. It’s a scam. A trap designed to harvest data and exploit trust.
The real story isn’t about nekoJB itself—it’s about how the jailbreak landscape has evolved. Apple has raised the bar, and the space left behind is being filled with scams and noise.
Ready to learn more about Corellium? Request a free trial or meet with our team today.
Keep reading

Mobile App Compliance: How Virtual Testing Speeds Regulatory Approval

Mobile App Security Checklist: A 30-Day Plan to Go From Zero to Secure

