Introducing MicroSnapshots - Leveraging copy-on-write memory
A powerful tool for rapid virtual machine state restoration
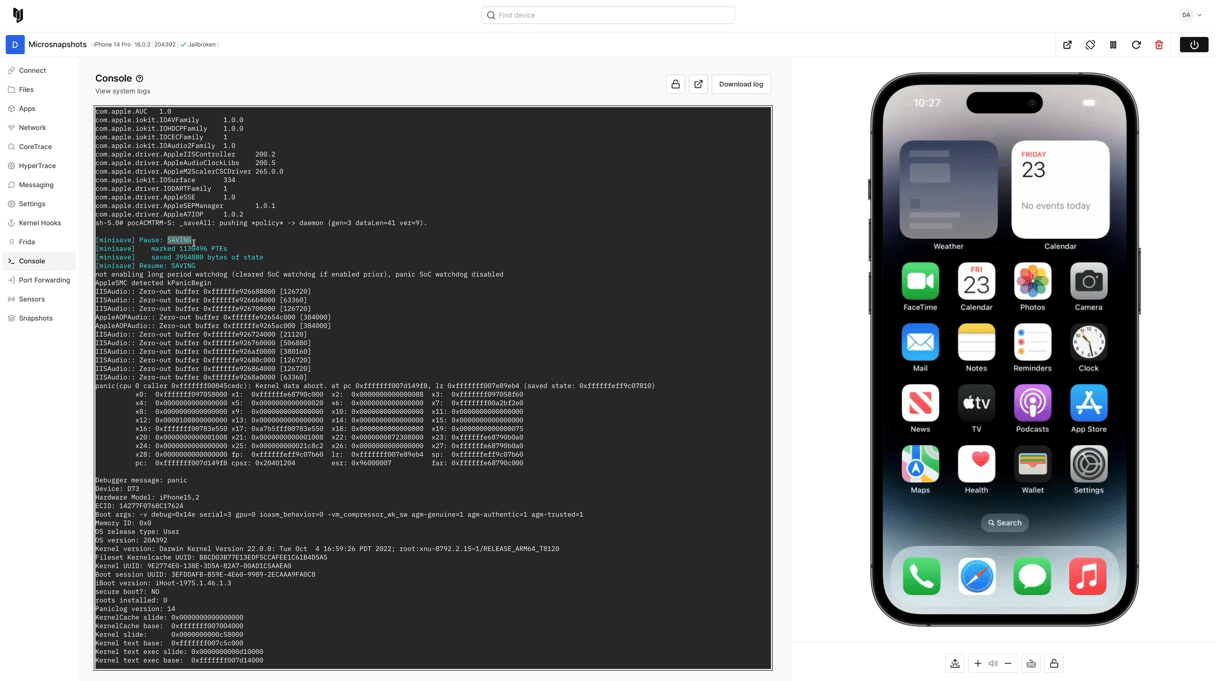
This video is a quick demonstration of the MicroSnapshots feature on Corellium, which provides programmatic rapid restoration of a virtual machine's state. This feature is primarily useful for snapshot fuzzing.
This feature is intended for relatively short cycles of saving and restoring the system state. Unlike full device snapshots, as seen in the Corellium user interface, which is more long-lived. MicroSnapshots use copy-on-write memory and other hypervisor features, allowing restoration to the starting state in as low as eight milliseconds, depending on how many memory pages were dirtied.
The API for this feature consists primarily of a fork hypercall and an exit hypercall, which restores the state back to the time of the fork.
First, perform any expensive initializations, such as opening a connection to a target IOKit driver. Since this happens before saving the state, this can reduce snapshot fuzzing overhead substantially.
Then, in a loop, fork the state with an optional timeout. Like the POSIX fork system call, the return value indicates whether the current code path is in the MicroSnapshot, or after restoring the state. If the result is zero then fetch a test case from some coordinator and call the IOKit method to fuzz. This will either panic or return, in which case the exit hypercall restores the saved state.
Based on the return value at this point, a panic can be detected and saved, coverage data from the test case can be recorded with Corellium CoreSight or HyperTrace, or other exceptional situations can be handled. Finally, the fork hypercall is executed again and the fuzzing cycle continues.
In the demo, a proof-of-concept vulnerability trigger is created for CVE-2023-28206, originally published by Linus Henze, which has been modified to run with MicroSnapshots so that after the kernel panic occurs, the state is restored, and the virtual device is usable again. The code demonstrates the hypercall API for retrieving the kernel panic data as a buffer. In a fuzzing context, this would be used to report a crash to a coordinator along with the test case and coverage data.
To make use of this feature with your on-premises Corellium Premium license, contact your Corellium representative and request the MicroSnapshots SDK.
The Corellium Virtual Hardware platform provides never-before-possible security vulnerability research for iOS and Android phones. Are you interested in learning more? See all our mobile security research capabilities.
Advance Your Mobile Security Research with Corellium
Experience Corellium’s groundbreaking virtualization technology for mobile devices and discover never-before-possible mobile vulnerability and threat research for iOS and Android phones. Book a meeting today to explore how our platform can optimize mobile security research and malware analysis.
Keep reading

Corellium Expands iOS 26 Testing with Risk Scoring and iPhone 17 Support

Apple's MIE Framework Makes Jailbreak-Dependent Testing Obsolete


