Runtime Application Security: From ASPM to Real-Time Detection
Everyone was talking about Application Security Posture Management (ASPM) at the RSA Conference, but here's what most people missed - the industry is already moving past it. The new focus? Runtime application security and Application Detection and Response (ADR).
For mobile apps, this shift changes everything. Traditional security scans miss the vulnerabilities that actually matter. You can scan mobile app code for weeks, but you'll never catch banking trojan behaviors, cryptocurrency theft patterns, or privacy violations until the app is actually running on a device.
That's the fundamental problem with static analysis - it looks at code sitting still, not code doing things.
Real-World Evidence: When Static Analysis Failed
Static analysis misses what actually happens when mobile apps run in the wild. These next examples show how runtime threats unfold—and why runtime detection and application detection and response are critical for catching them. This is where runtime application security proves its value.
Case Study 1: Crocodilus Banking Trojan Goes Global (March 2025)
This sophisticated banking trojan perfectly demonstrates how runtime behavior detection is essential for modern mobile security.
What happened: Security researchers discovered Crocodilus, an Android banking trojan that expanded from targeting users in Spain and Turkey to operating in 8 countries including Argentina, Brazil, India, Indonesia, and the United States. The malware masqueraded as legitimate apps like Google Chrome while conducting overlay attacks against financial applications.
Why static analysis missed it: The trojan appeared as a legitimate browser update or casino app in static analysis. However, during runtime, it retrieved lists of targeted financial apps from external servers, launched sophisticated overlay attacks to harvest credentials, and used accessibility services to capture cryptocurrency wallet seed phrases.
The impact: The trojan successfully stole banking credentials and cryptocurrency wallet information from users across multiple countries, demonstrating how runtime-based attacks can evade traditional security measures and operate at scale.
Unlike traditional static analysis that only examines code at rest, Corellium's runtime analysis capabilities would have immediately flagged this banking malware during behavioral testing. CoreTrace's real-time system call monitoring would have detected the trojan's suspicious activities: unauthorized network connections to external command servers, overlay window creation attempts, and accessibility service abuse for credential harvesting. This dynamic analysis approach catches malware that appears legitimate in static scans but reveals malicious intent during execution.

Corellium CoreTrace interface demonstrating real-time system call monitoring during mobile app security analysis
Case Study 2: Candy Crush and Tinder Location Data Breach (January 2025)
This case perfectly illustrates how privacy violations occur during runtime, not in static code analysis.
What happened: A major security incident occurred when a popular location data broker suffered a data breach that exposed vast amounts of user location data sourced from popular apps including Candy Crush and Tinder. The breach involved terabytes of consumer data stored in Amazon cloud servers and included sensitive locations like government and military sites.
Why static analysis missed it: Static analysis of Candy Crush and Tinder would show legitimate location permission requests and proper API usage. The privacy violation occurred during runtime when these apps continuously transmitted precise location data to third-party brokers without users' full understanding of how this data was being collected, stored, and potentially exposed.
The impact: Millions of users had their precise location histories exposed, including visits to sensitive locations. The breach demonstrated how legitimate-seeming apps can create massive privacy risks through their runtime data collection and sharing practices.
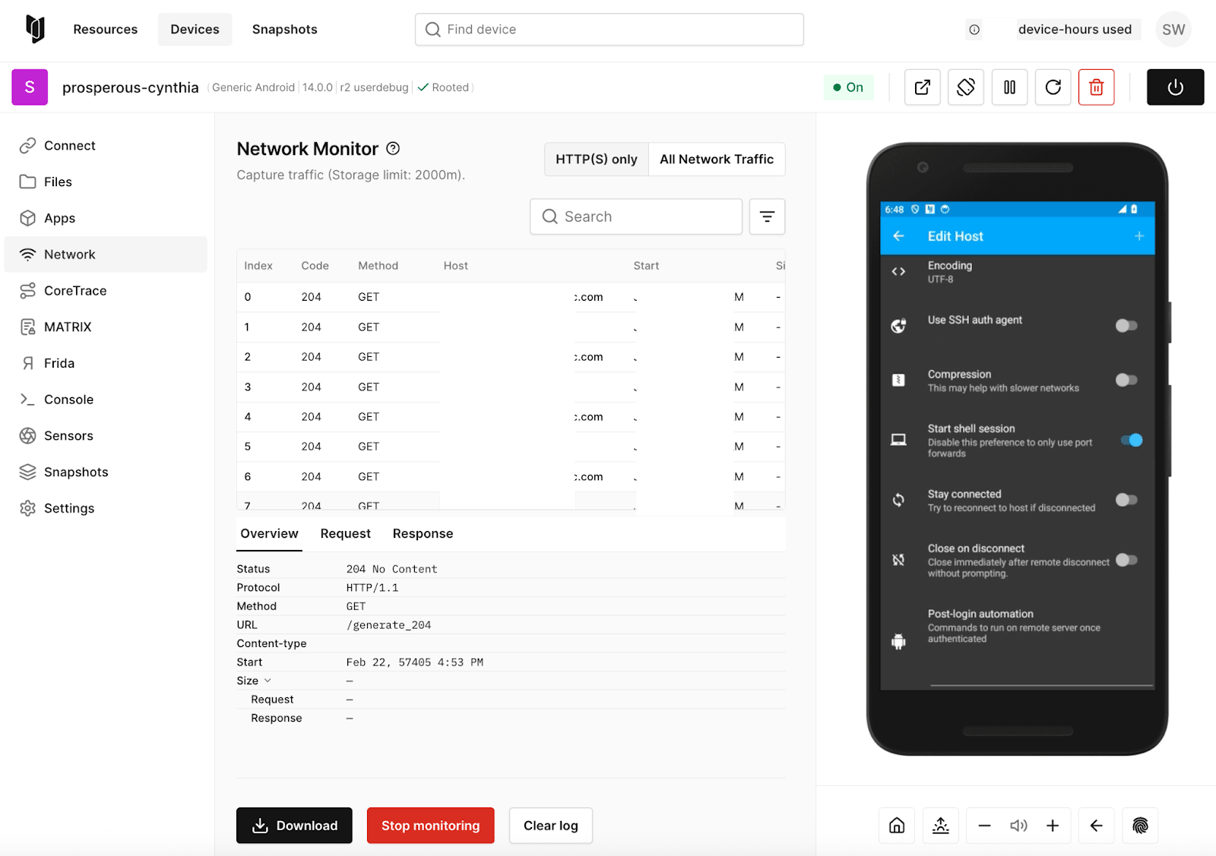
While static analysis would only show legitimate location permission requests, Corellium's Network Monitor would have revealed the true scope of data collection during runtime. By capturing real-time network traffic, security teams could have identified the continuous transmission of precise location coordinates to unexpected third-party servers, including the frequency and granularity of data being shared. This runtime visibility would have exposed the gap between user expectations and actual data practices, allowing organizations to detect privacy violations before they become major security incidents.

Corellium Network Monitor interface capturing real-time location data transmission patterns from mobile apps to third-party servers.
The Traditional Testing Problem
Here's why traditional mobile security testing fails:
Physical Device Limitations:
- Need multiple devices across different manufacturers and price points
- Can't safely test banking trojans without compromising devices
- Expensive to maintain international device variants for global threat testing
- Unable to simulate supply chain compromises in controlled environments
Static Analysis Blind Spots:
- Misses overlay attack mechanisms that only appear during app interactions
- Can't detect address-swapping behaviors in cryptocurrency transactions
- Doesn't catch excessive location data transmission patterns
- Fails to identify malicious update hijacking techniques
Periodic Testing Windows:
- Security testing happens before release, not during active usage
- No visibility into how apps behave in different geographical regions
- Vulnerabilities discovered after users are already compromised
- No way to detect evolving attack patterns in deployed applications
Enter Runtime Security: The Game Changer
Runtime security monitoring watches apps while they're actually running and interacting with users. Instead of scanning static code, it observes live behavior patterns. This catches entire categories of attacks that static analysis can't touch.
The documented evidence from 2025 shows that sophisticated attacks are consistently missed by static analysis but revealed through runtime monitoring. Crocodilus's overlay attacks, supply chain crypto theft, and location data privacy violations were all discovered through runtime observation of actual app behavior.
How Corellium Enables Real-Time Detection
Traditional mobile security testing requires physical devices, manual setup, and region-specific configurations. Corellium changes this completely by providing virtual iOS and Android devices that can simulate global attack scenarios continuously.
Real-Time Behavioral Pattern Recognition
With Corellium's CoreTrace feature, security teams can monitor complex behavioral patterns while apps are running:
- Banking overlay attack detection (like Crocodilus's credential harvesting)
- Cryptocurrency address manipulation monitoring (like the supply chain clipping attacks)
- Location data transmission analysis (like the Candy Crush/Tinder privacy violations)
- Accessibility service abuse detection
- Supply chain integrity verification
Advanced Network Traffic Analysis
Corellium's built-in network monitoring captures sophisticated attack communications:
- Command-and-control server interactions for retrieving target lists
- Real-time detection of wallet address substitution
- Location data broker communication patterns
- Encrypted payload analysis for malicious updates
Global Attack Simulation
Unlike traditional testing that focuses on local threats, Corellium enables comprehensive monitoring:
- Simulate banking trojans across multiple countries simultaneously
- Test supply chain attacks on various device configurations
- Monitor privacy violations across different app usage patterns
- Detect region-specific attack variations in real-time
The Future of Mobile Security
The shift from static to runtime security isn't just a trend - it's a necessity. The documented case studies from 2025 show that sophisticated attacks consistently evade static analysis but get caught by runtime monitoring.
Static analysis will always have a place for catching basic coding errors and known vulnerability patterns. But for finding the attacks that actually succeed in the wild - the behavioral manipulation techniques, the supply chain compromises, the privacy violations - you need runtime monitoring.
That's why leading security teams are moving away from periodic security audits toward continuous runtime monitoring. They're not just scanning code anymore; they're watching behavior patterns that indicate real attacks.
Making Runtime Security Practical
The challenge with runtime security has always been scale and complexity. How do you monitor sophisticated attack patterns across global threat landscapes without massive infrastructure overhead?
Corellium solves this by providing:
- Global virtual device simulation: Test attack patterns across different regions and device configurations
- Built-in behavioral analysis: Advanced monitoring tools that detect complex attack techniques automatically
- Continuous threat intelligence: Monitor evolving attack patterns without physical device constraints
- Safe attack simulation: Test dangerous malware behaviors without contaminating real infrastructure
The Bottom Line
Application Security Posture Management was about understanding what vulnerabilities exist in your code. Runtime application security is about understanding what attack behaviors exist in your running applications - and catching new attack patterns as they emerge globally.
The evidence from 2025 is clear: Crocodilus's global banking attacks, supply chain cryptocurrency theft, and privacy violations in popular apps were all discovered through runtime behavioral analysis, not static code scanning. Each incident affected millions of users and caused significant financial and privacy damage.
For mobile security, this shift is already happening. The teams that adapt to runtime monitoring will detect attack patterns others miss. The teams that stick with static analysis only will keep missing the behavioral attacks that actually succeed.
The question isn't whether to adopt runtime security monitoring - it's how quickly you can implement it before the next sophisticated attack campaign targets your users.
To learn more, book a meeting with our team or request a free trial of Corellium Viper today.
Keep reading

Mobile App Compliance: How Virtual Testing Speeds Regulatory Approval

Mobile App Security Checklist: A 30-Day Plan to Go From Zero to Secure

