Apple signing with Corellium

Introduction — iOS security testing woes
Want to sideload your iOS application for mobile security testing? Or do you want to pass your application to QA, dev or third-party teams? Are you struggling with binary signing and consistent errors? This article will help you to build the necessary knowledge to avoid these errors.
Apple developer accounts
Apple offers two programs a team can enroll in, the Apple Enterprise (~$300) and the Apple Developer Program (~$100). In order to sign an iOS application, it is required to be enrolled in one of their developer programs. Each one has pros and cons, and simple mistakes with either can lead to errors when installing iPA files.
Apple Enterprise program
The Apple Enterprise program allows you to create an iOS Distribution Certificate that can run on target devices without being published to the App Store and without knowing the device UDID on which the app will be installed and ran.
This method is typically used within an enterprise environment where an application is developed and then shared with various internal or external teams and you might not know the UDID of every device that is going to be used.
Apple Developer program
The Apple Developer program allows you to create an additional iOS Distribution Certificate that will allow you to roll out to the App store which cannot be done using the certificate from the Enterprise Program.
You can also create custom certificates which can be distributed to your test devices. It’s important to note that these devices must be registered in the Apple Developer Portal (UDID) and be associated with that specific certificate via the iOS provisioning profile.
What do I choose? Do I need enterprise?
If your team has to create staging builds, QA, Security testing and more for various groups without registering their device IDs, you used to have to enroll in both programs. The enterprise program was used to manage the distribution without knowing the team’s device IDs, and the developer program was used to manage the certificate that would ultimately be pushed to the App store.
Enter Corellium iOS virtual machines
Using Corellium virtualized iOS devices, you can avoid those errors when side loading iOS applications that have invalid signing signatures or don’t have the specific test device UDID registered. Corellium allows you to modify your device UDID to match a physical device you already have registered with your signing certificate.
When side loading iOS applications on Corellium virtualized devices, have you run into errors? These happen because most teams continue to use the Apple Developer Program for their applications and are not aware of the UDID of every device they are installing the application on.

How to fix these errors with Corellium
Using Corellium and having the ability to change your device UDID is the key to solving these errors when side loading applications.
This process starts with identifying which devices are registered for your application.
1. Unzip the application IPA to identify the devices within the provisioning file used.
unzip Corellium_Signing_Test.ipa
2. Navigate to the “Payload Directory”
3. Open the *.app directory [If you are using finder (mac) you will need to right click and “Show Package Contents”]
4. In this directory will be a file “embedded.mobileprovision” file; this is an XML file that you can use a text editor to view (or you view it through Xcode on a mac).
Once you have opened the “embedded.mobileprovision” file, you will see the Provisioned Devices.
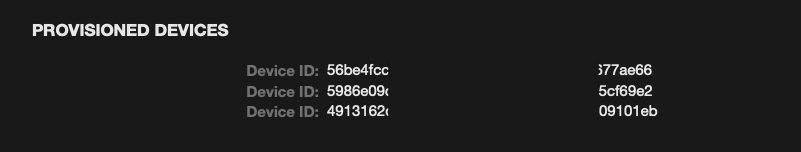
Copy one of the UDIDs for a provisioned device and navigate to the following section within Corellium to update your virtualized device UDID:
iOS Device > Settings > Device IDs > UDID Field
Once you have updated the device UDID with that of a provisioned device from the app’s provisioning file, you will be able to successfully install the application to your virtualized device without a signing error.

Additional troubleshooting options to enable iOS security testing on virtual machines
If, for any reason, you are still unable to install your application to your virtualized device there is an additional option that will allow you to disable/bypass iOS application signature verification.
This involves using a Cydia package – AppSync Unified. AppSync Unified is a Cydia tweak that allows users to install ad-hoc signed, fake signed, unsigned, or expired IPA app packages on their iOS devices without receiving signing errors.
AppSync Unified is available from Karen's Repo.
How does it work?
When iOS makes a request to install an application (depending on the iOS version), a function will be called and ApSync Unifieds injected functions will take over. If the signing is invalid in any way, the hooked functions will bypass Apple’s checks and allow you to install the app without error.
Once you have the Cydia package installed, every IOS application you attempt to install will be checked for invalid signing and, as mentioned above, if it is invalid, the checks will be bypassed and the binary will install without error.
Keep reading

Mobile App Compliance: How Virtual Testing Speeds Regulatory Approval

Mobile App Security Checklist: A 30-Day Plan to Go From Zero to Secure

