The Calls Are Coming from Inside the House

When investigating targeted exploits or phishing attacks, it's essential to recreate the attacker's perspective as closely as possible. In some cases, this may require a remote virtual iOS device to access the internet through your local IP address, as attackers might only serve malicious pages when the incoming IP matches their expected target. Setting up a reverse tunnel can help you achieve this and gain valuable insights into the attacker's tactics.
In this blog post, we'll walk you through the process of setting up a reverse tunnel to allow a remote virtual iOS device to access the internet through your local IP address. We'll cover the following topics:
- What is a reverse tunnel?
- Installing and configuring the GOST proxy server
- Setting up the reverse tunnel with SSH
- Testing the reverse tunnel
1. What is a reverse tunnel?
A reverse tunnel is a technique used to forward a remote machine's port to your local machine, effectively allowing the remote machine to access resources on your local network. This can be especially useful when dealing with remote virtual devices or systems that are behind firewalls or have limited connectivity options.
In our scenario, we want to set up a reverse tunnel so that a remote virtual iOS device can access the internet through our local IP address. To achieve this, we'll need to install and configure a proxy server on our local machine and then create a reverse tunnel using SSH.
2. Installing and configuring the GOST proxy server
To set up the proxy server on our local machine, we'll be using the GOST proxy server. GOST is a simple yet powerful proxy server written in Go that supports a variety of proxy protocols, including HTTP, HTTPS, and SOCKS. We're going to stick with GOST v2, as while GOST v3 does appear to be stable, I prefer to stick with projects with a larger critical mass when it comes to networking.
This blog post assumes you have Go already installed; if not, you can find a guide here.
To get started, first clone the GOST repository from GitHub using the following commands:
```sh
git clone https://github.com/ginuerzh/gost.git
cd gost/cmd/gost
Once you have the repository cloned, build the Gost binary using the go build command:
```sh
go build
```
Now that we have the GOST binary built, we can start the proxy server by running the following command:
```sh
./gost -L http://127.0.0.1:31337
```
This will start the Gost proxy server, listening on port 31337 of your local machine's loopback address (127.0.0.1). We're using HTTP as that's what iOS supports. For those wondering, this is still encrypted, despite being "HTTP"; we're tunneling an encrypted HTTPS connection over an unencrypted HTTP connection encrypted SSH connection over an encrypted SSH connection.
3. Setting up the reverse tunnel with SSH
With the GOST proxy server running on our local machine, we can now set up the reverse tunnel using SSH. First, you'll need to grab the "Quick Connect" SSH command.
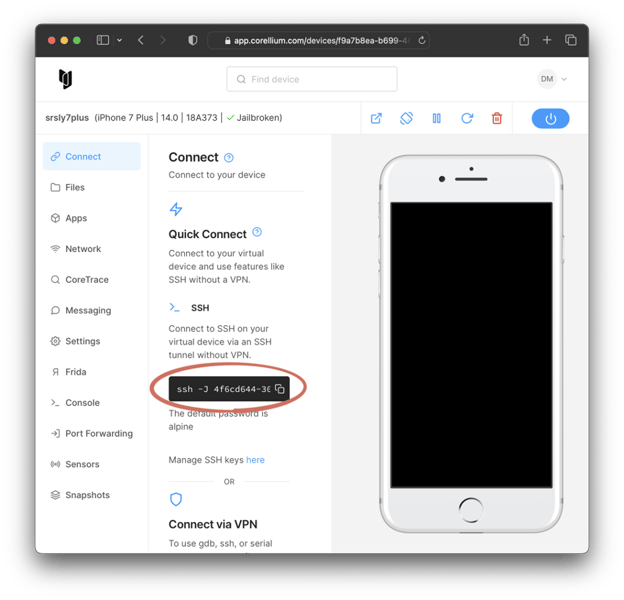
Then, we'll modify the command slightly:
```
ssh -R 127.0.0.1:31337:127.0.0.1:31337 -J 4f6cd644-3065-45f6-b5b9-9156929d8f82@proxy.corellium.com root@10.11.1.1
```
Let's break down what this command does:
`-R 127.0.0.1:31337:127.0.0.1:31337`: This flag sets up the reverse tunnel, forwarding the remote port 31337 to the local port 31337.
`-J 4f6cd644-3065-45f6-b5b9-9156929d8f82@proxy.corellium.com`: This flag specifies the SSH jump host (proxy server) to use when connecting to the remote machine. In this case, we're using the provided Corellium proxy server.
By executing this command, the reverse tunnel will be established, allowing the remote virtual iOS device (root@10.11.1.1) to access the internet through your local IP address.
You should now notice connections begin to immediately trickle in.
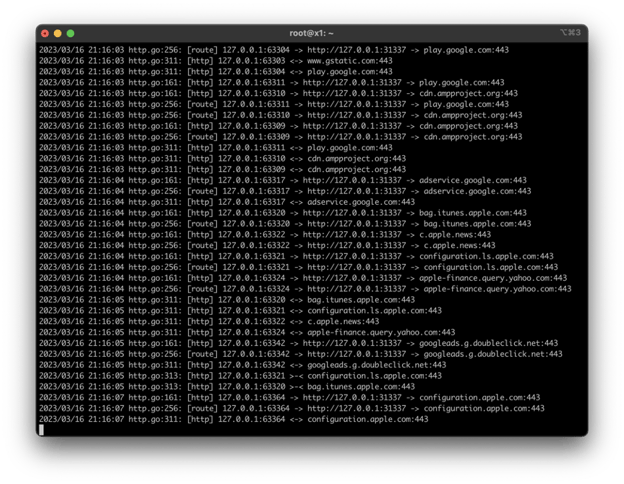
4. Testing the reverse tunnel
Now that we have the reverse tunnel set up, let's test it to ensure everything is working correctly. To do this, we'll need to configure the remote virtual iOS device to use the GOST proxy server for its internet connection.
On the remote virtual iOS device, open the Settings app and navigate to the Wi-Fi settings. Here, tap on the connected Wi-Fi network and scroll down to the "HTTP Proxy" section. Choose "Manual" and enter the following information:
Server: 127.0.0.1
Port: 31337
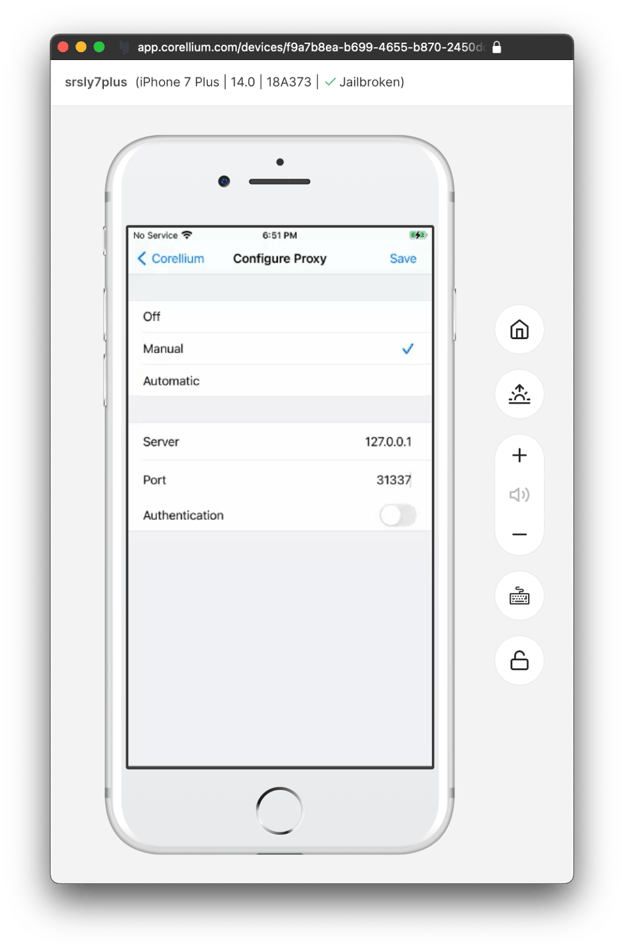
Save the changes and exit the settings. The remote virtual iOS device should now be using the GOST proxy server for its internet connection, effectively accessing the internet through your local IP address.
To verify that the reverse tunnel is working as expected, try opening a web page that echoes your IP back, or uses IP geolocation. As seen in the screenshot below, the network traffic is indeed being routed through my local machine. We're now ready to click on every sketchy link that comes in through an anonymous Telegram message!
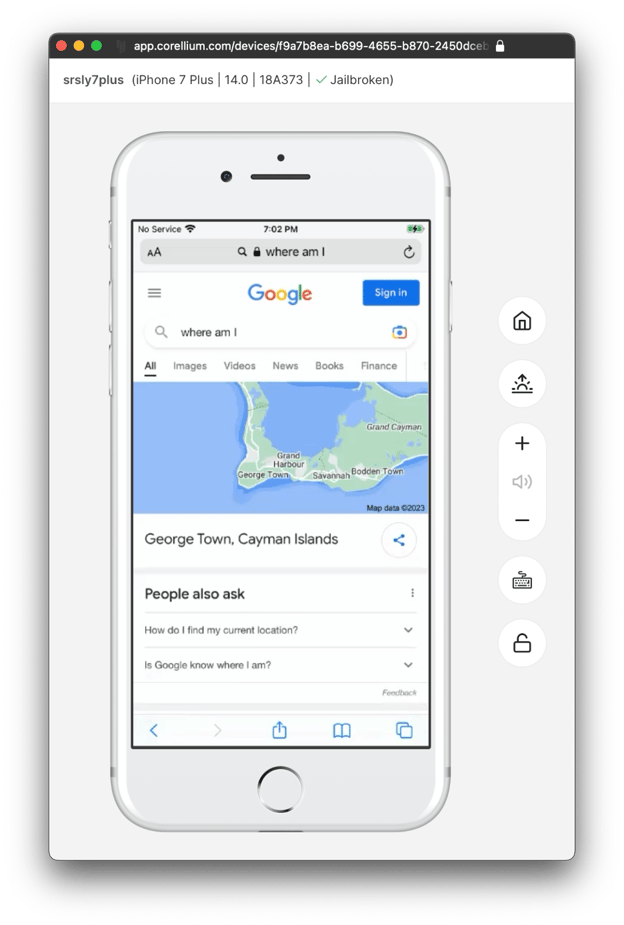
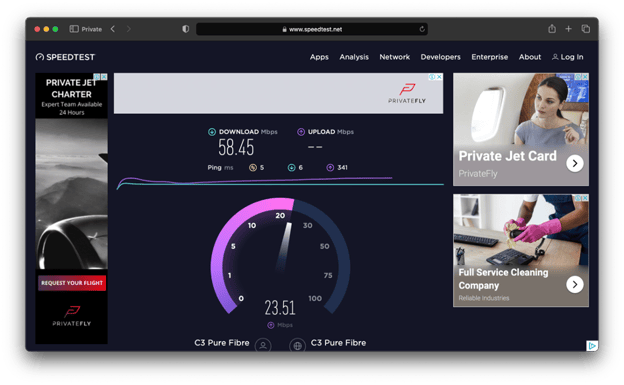
The performance is shockingly good too.

(You'll also notice I'm now getting targeted ads to assist with immigrating to Canada, which always makes me chuckle as a Canadian citizen.)
For reference, this is only about 1Mbps slower than my upload speed.
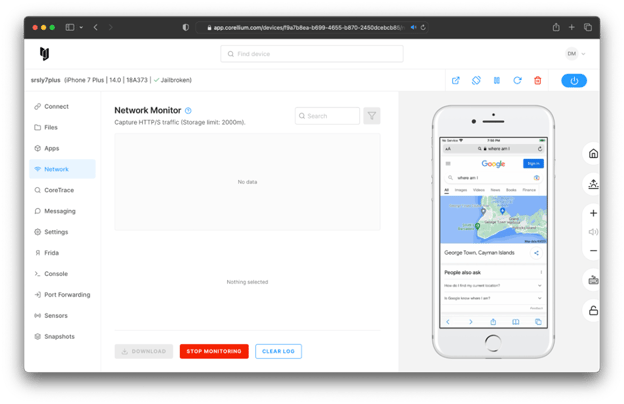
One minor note is that this proxy setup does bypass the "Network Monitor" feature built-in to Corellium. If you want to capture traffic (which you should), you'll need to set up a tool like mitmproxy on your local machine.
5. Understanding the risks associated with reverse tunnels
By creating a reverse tunnel, you are essentially opening a door into your local network. In practice, LAN side access to your typical shoddy ISP immobile odem may be enough for your "typical" APT to get a persistent foothold.
Basically, think of this like sharing your WiFi password. You probably trust your coworker on your LAN. You probably don't trust your friend James Willy from North Korea. If you have more "friends" that fall into the latter category, I would encourage you to run GOST on a mobile network, completely isolated from any of the networks you actually use personally.
In a future blog post, we'll cover setting up GOST on a physical mobile device with an LTE connection, and routing the proxy back through a wired connection. Until then, happy fishing!
Keep reading

Mobile App Security Risks: The Hidden Threat in Your App Supply Chain

What Is Security Debt? The Hidden Cost of Delaying Mobile App Security

