Bypass Boolean-Based iOS Jailbreak Detection with Frida
Jailbreak detection algorithms serve as a powerful barrier in the world of iOS security, preventing users with jailbroken devices from accessing all mobile apps in the App Store. While this improves device security, it can also make security testing for iOS applications impossible, constricting the scope of analysis.
This blog post explores the start of an interesting topic, avoiding jailbreak detection for iOS applications. This post will use the iOS DVIA-2 (Damn Vulnerable Application). We will start with a beginner method for jailbreak bypasses by looking at the app's classes and using the capabilities of Corellium's virtualized platform rather than relying on physical devices.
We walk you through the process of setting up Corellium's virtualized device environment, examining the pertinent DVIA-2 classes, and how to bypass jailbreak detection. By following along, you'll discover approaches that may be used with different apps and useful insights into how iOS applications function.
Please be aware that this blog post's sole goal is education, written with researchers, developers, and iOS security enthusiasts in mind. Respecting the limits set by developers and application providers and abiding by ethical standards are crucial.

What Is Boolean-Based Jailbreak Detection?
Boolean-based jailbreak detection refers to a method within an iOS app that checks whether the device it’s running on has been jailbroken and returns a simple true or false value. These checks are typically implemented using one or more telltale signs of a physical jailbreak, such as the presence of certain files (e.g. /Applications/Cydia.app), the ability to write outside the app sandbox, or the use of forbidden syscalls.
From a mobile app security research perspective, these checks can block access to critical app functionality, hindering dynamic analysis and reverse engineering. For this reason, bypassing Boolean-based detection logic is a foundational step for penetration testers, particularly those focused on privacy and data flow analysis.
Why Use Corellium for Frida-Based Bypass Testing?
Corellium offers a purpose-built platform that dramatically simplifies the process of bypassing jailbreak detection on iOS apps. Unlike physical devices (which require extensive setup, jailbreaking, and provisioning) Corellium lets developers and researchers:
- Spin up pre-jailbroken virtualized iOS devices on multiple versions
- Use a built-in Frida console with no manual injection needed
- Save and restore environments to test the same bypass under different conditions
- Collaborate easily across teams without sharing hardware
This makes Corellium uniquely valuable for mobile app pentesting workflows, especially those involving instrumentation tools like Frida.
Setup and Configuration
To get started with the DVIA-2 application, we must download the iPA and set up a virtualized iOS jailbroken device for us to work with.
The DVIA-2 application can be downloaded here.
Once you have the iPA, in Corellium, you will need to set up an iOS device, for this exercise, I will be using an iPhone 7 Plus on 15.7.1. However, Corellium supports the latest iOS and iPadOS such as iOS 26 and latest iPhone 17 builds.
Once the device is created and booted up, we can install the DVIA-2 iPA that we obtained above. That can be installed easily through the “Files” tab on the left of Corellium.

Identifying Classes – Jailbreak Test 2
You can now launch the DVIA-2 application from your device and navigate to the “Jailbreak Detection” menu. We will be working on challenge 2 to look at classes. The other challenges require more in-depth reverse engineering, which I will cover in a separate blog post.
The first thing we need to do is identify the classes within the DVIA application that are responsible for jailbreak detection. The following Frida script can be used to either dump all class names (if the search field is blank) or search for a specific search time like I am below (looking for Jailbreak).
var search_class = ['Jailbreak'];
if (ObjC.available)
{
for (var className in ObjC.classes) {
if (Array.isArray(search_class) && search_class.length) {
for (var i = 0; i < search_class.length; i++) {
if
(className.toLowerCase().includes(search_class[i].toLowerCase())) {
console.log(className)
}
}
}
else {
console.log(className);
}
}
}
The above script can be added into the Frida console within Corellium. From the Frida tab attach to the DVIA application (make sure the app is running) and execute the script.
![]()
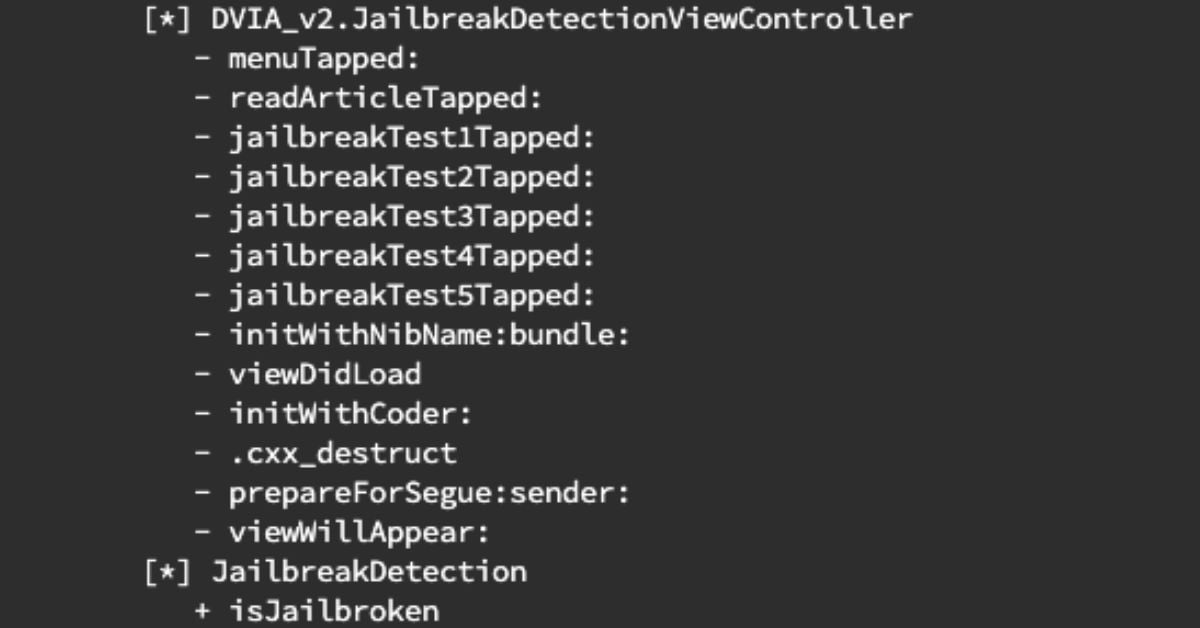
Once the script has been executed, you should see the following classes within the DVIA-2 application relating to “Jailbreak”
![]()
Identifying iOS Jailbreak Bypass Detection Methods
Now that we have a good idea of what class is being used for Jailbreak detection (JailbreakDetection), we can start looking at the methods that are used. The following script can be used to enumerate methods to a specific class name (set at the beginning of the script).
var search_class = ['JailbreakDetection'];
var search_method = [''];
function print_methods(className) {
var methods = ObjC.classes[className].$ownMethods;
if (Array.isArray(search_method) && search_method.length) { //search_method not empty
for (var j = 0; j < search_method.length; j++) {
if (methods.join('
').toLowerCase().includes(search_method[j].toLowerCase())) {
console.log('[*] ' + className);
for (var i = 0; i < methods.length; i++){
if
(methods[i].toLowerCase().includes(search_method[j].toLowerCase())) {
console.log(' ' + methods[i]);
}
}
}
}
}
else {
console.log('[*] ' + className);
var methods = ObjC.classes[className].$ownMethods;
for (var i = 0; i < methods.length; i++){
console.log(' ' + methods[i]);
}
}
}
if (ObjC.available)
{
for (var className in ObjC.classes) {
if (Array.isArray(search_class) && search_class.length) { // search_class not empty
for (var i = 0; i < search_class.length; i++) {
if
(className.toLowerCase().includes(search_class[i].toLowerCase())) {
print_methods(className);
}
}
}
else {
print_methods(className);
}
}
}
We need to run this script against the DVIA-2 application in the Frida console within Corellium using the same methods we did above. The results should be similar to the following:
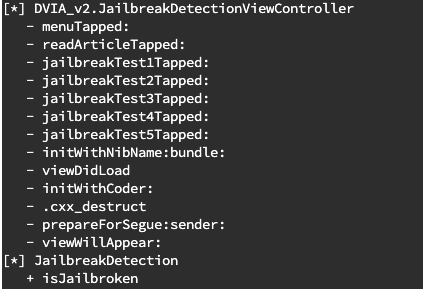
The one we are looking for in this situation is the following method under the JailbreakDetection class:
+ isJailbroken
Hooking Methods to Modify Results
So now that we have the class and the method, we need to hook it to see what is being returned. Below is a script we can use:
Note: This script can be utilized for multiple apps. Just make sure to update the class and function to reflect the app you are testing.
if (ObjC.available) {
try { var className = "JailbreakDetection";
var funcName = "+ isJailbroken";
var hook = eval('ObjC.classes.' + className + '["' + funcName + '"]');
Interceptor.attach(hook.implementation, {
onLeave: function(retval) { console.log("[*] Class: " + className);
console.log("[*] Method: " + funcName);
console.log("\t[-] Return value Type: " + typeof retval);
console.log("\t[-] Value: " + retval); } }); }
catch(err) { console.log("[!] Exception: " + err.message); } }
else { console.log("Objective-C Runtime is not available"); }
We can run this script within the Corellium platform; unlike the two scripts we ran above, this script will require user interaction after it is run. When running it, click the “Jailbreak Test 2” within the DVIA-2 application to see the results (should be similar to below).
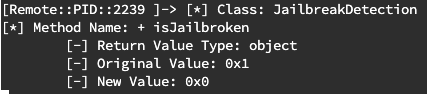
If you selected any other test within the DVIA-2 application, you won’t see the results because their implementations require some more in-depth reverse engineering. Sticking to the “Jailbreak Test 2” will ensure it continues to work.
Modifying the Values
Now that we got a Boolean value of 1 getting returned, we need to focus on writing a script to flip that to bypass the jailbreak detection. Below is the script we can use:
Note: similar to the above script, this can be used for other apps if you change the class name, function name and the value to modify.
if (ObjC.available) {
try {
var className = "JailbreakDetection";
var funcName = "+ isJailbroken";
var hook = eval('ObjC.classes.' + className + '["' + funcName + '"]');
var newretval = ptr("0x0");
Interceptor.attach(hook.implementation, {
onLeave: function(retval) { console.log("[*] Class: " + className);
console.log("[*] Method Name: " + funcName);
console.log("\t[-] Return Value Type: " + typeof retval);
console.log("\t[-] Original Value: " + retval);
retval.replace(newretval)
console.log("\t[-] New Value: " + newretval) } }); }
catch(err) { console.log("[!] Exception: " + err.message); } }
else { console.log("Objective-C Runtime is not available"); }
When you run this script and click “Jailbreak Test 2,” you will notice that the device is no longer shown as jailbroken.

Hopefully this helps you learn the basics of Frida scripting for iOS applications. Please watch for upcoming webinars and blog posts to go more in-depth with Frida scripting, iOS reverse engineering, and more.
Next Steps: Advanced Frida Scripting and Swift Binary Analysis
Once you’ve mastered basic method hooking, the next frontier is advanced scripting and binary-level inspection:
- Objection: A runtime exploration toolkit for Frida with built-in bypass modules
- Swift name demangling: Necessary for reverse engineering Swift-based detection logic
- Instruction-level hooking: When function names aren’t available, you may need to hook memory offsets or CPU register changes
- Frida gadget or early-loading techniques: For scenarios where detection logic executes before you can attach Frida
These methods enable deeper analysis, especially against hardened or obfuscated apps. Teams can gain comprehensive visibility into runtime behaviors of mobile apps, particularly to identify security issues like insecure data storage, flawed encryption, privacy violations, and bypassed business logic.
Unlock Superior Mobile Security Testing with Corellium
Equip your security teams with unprecedented tools for both manual and automated testing, freeing up valuable engineering time and saving money. Discover the power of Corellium’s high-fidelity virtual devices and spin-up near limitless combinations of device and OS with one-click jailbreak/root access. Set up a meeting today to see how we can streamline your processes and reduce costs. Want to try this in a virtual environment? Get a free trial today.
Keep reading

Corellium Expands iOS 26 Testing with Risk Scoring and iPhone 17 Support

Apple's MIE Framework Makes Jailbreak-Dependent Testing Obsolete

