The Corellium Resource Library
The latest articles and news on mobile app security testing, IoT and research from Corellium and community contributors.

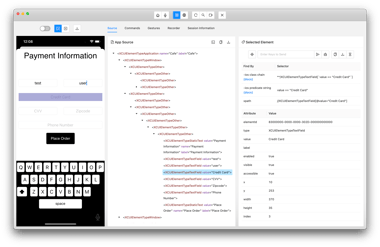
How Third-Party SDKs and APIs Create Mobile Supply Chain Security Risk
Load More
Subscribe to Stay Connected
Keep up to date with emails for the latest product news and technical articles.













































































































.png?length=380&name=Corellium+Arm_Blog_Post_Image_v1%20(1).png)