The Corellium Resource Library
The latest articles and news on mobile app security testing, IoT and research from Corellium and community contributors.

Beth Barach •
Sep 16, 2025
Common Vulnerabilities and Exposures Examples in Mobile Application Testing
Vulnerabilities and exposures are easier to share but testing mobile apps for them has never been more difficult.

Jason Yamada •
Sep 15, 2025
Embedded Debugging with Arm DS IDE: Secure Tools & Techniques for App Developers
A step-by-step guide to debugging bare-metal embedded software on Corellium Atlas with Arm DS IDE, from device setup to advanced debugging techniques.

Swaroop Yermalkar •
Aug 22, 2025
OWASP Mobile Security Testing: How Virtual Devices Catch What Top 10 Checks Miss
See how virtual iOS devices efficiently helps uncover threats that OWASP Top 10 mobile security testing often misses.

Brian Robison •
Aug 21, 2025
Complete Guide: The Ins and Outs of Automated Mobile Application Security Testing
Enhance protection with this mobile application security testing guide. Learn how automated application security testing secures Android and iOS apps.
Corellium •
Aug 20, 2025
Corellium MATRIX: Automated MAST Testing for Mobile Security
Discover how MATRIX automates MAST testing, enhances mobile app security, and simplifies compliance without relying on physical devices.
Beth Barach •
Aug 11, 2025
How Stronger Security for Mobile OS Creates Challenges for Testing Applications
Why you should develop and test on a virtual hardware platform: reason #4 stronger operating system security results in less secure testing.
Beth Barach •
Aug 11, 2025
Healthcare Mobile App Development: Mergers and Acquisitions Increase Risks
Leverage a virtual hardware platform for thorough mobile app testing for data leakage and exposure

Jason Yamada •
Aug 08, 2025
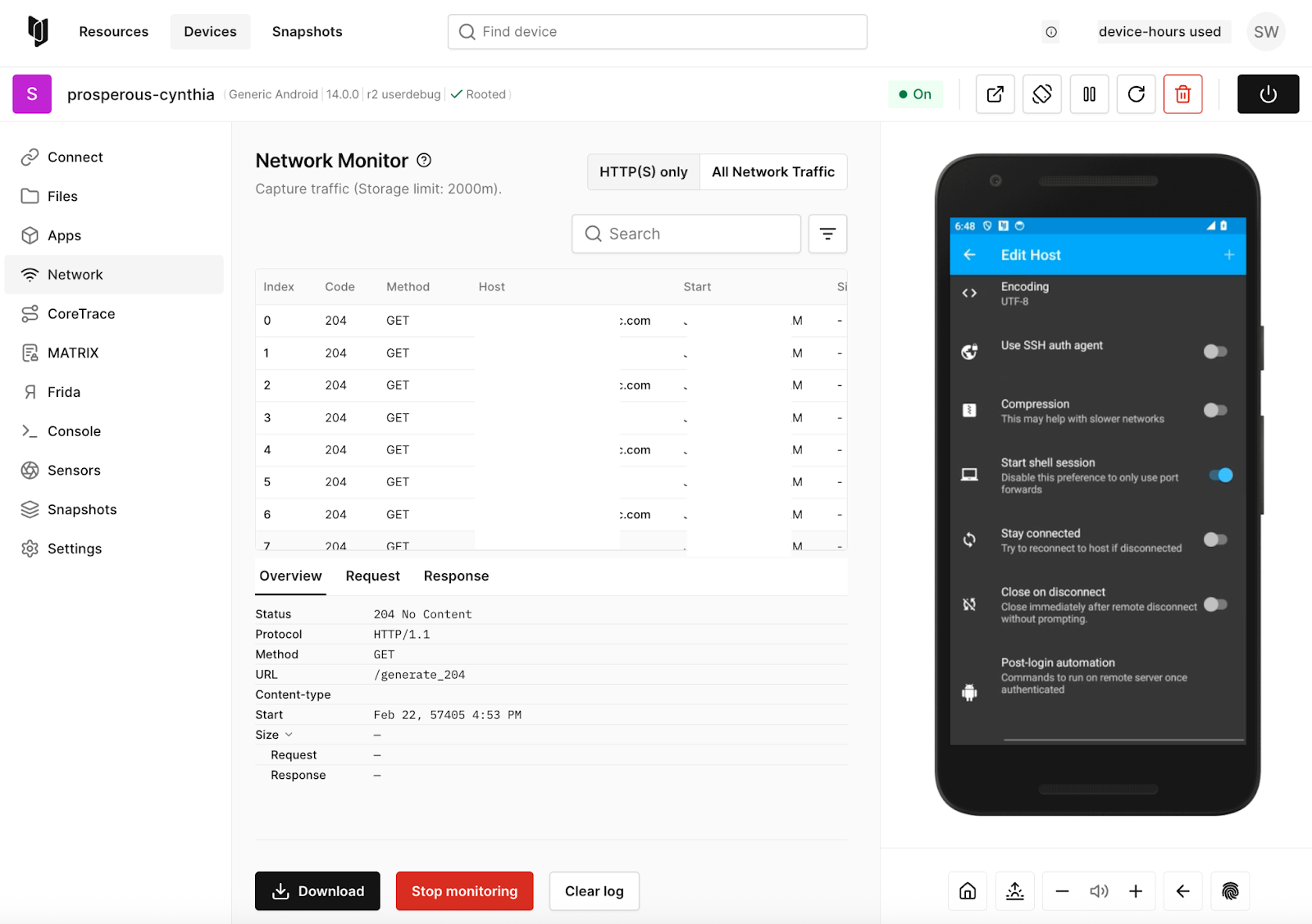
Building a Firmware Package for Corellium Atlas
Learn how to build and upload custom firmware packages for a variety of supported devices on the Corellium Atlas virtual hardware platform, including Raspberry Pi 4B, i.MX93, and more.
Swaroop Yermalkar •
Aug 06, 2025
Runtime Application Security: From ASPM to Real-Time Detection
Static analysis misses key mobile threats. Corellium’s runtime application security catches what ASPM can’t—delivering real-time protection.
Brian Robison •
Aug 05, 2025
Jailbreak iOS 18 on Corellium: What Testers Need to Know
The Corellium Virtual Hardware platform now supports iOS 18, including fully jailbroken iOS 18.

Beth Barach •
Aug 05, 2025
Rethink Your Approach to Secure Mobile Application Development
Secure testing starts here—explore the first of five insights into how virtual hardware changes the game.

Beth Barach •
Jul 17, 2025
Depth and Breadth Matters in Mobile Application Security Testing Scans
Why you should develop and test on a virtual hardware platform reason #3: MAST is not enough.
Subscribe to Stay Connected
Keep up to date with emails for the latest product news and technical articles.
