Workshop Overview
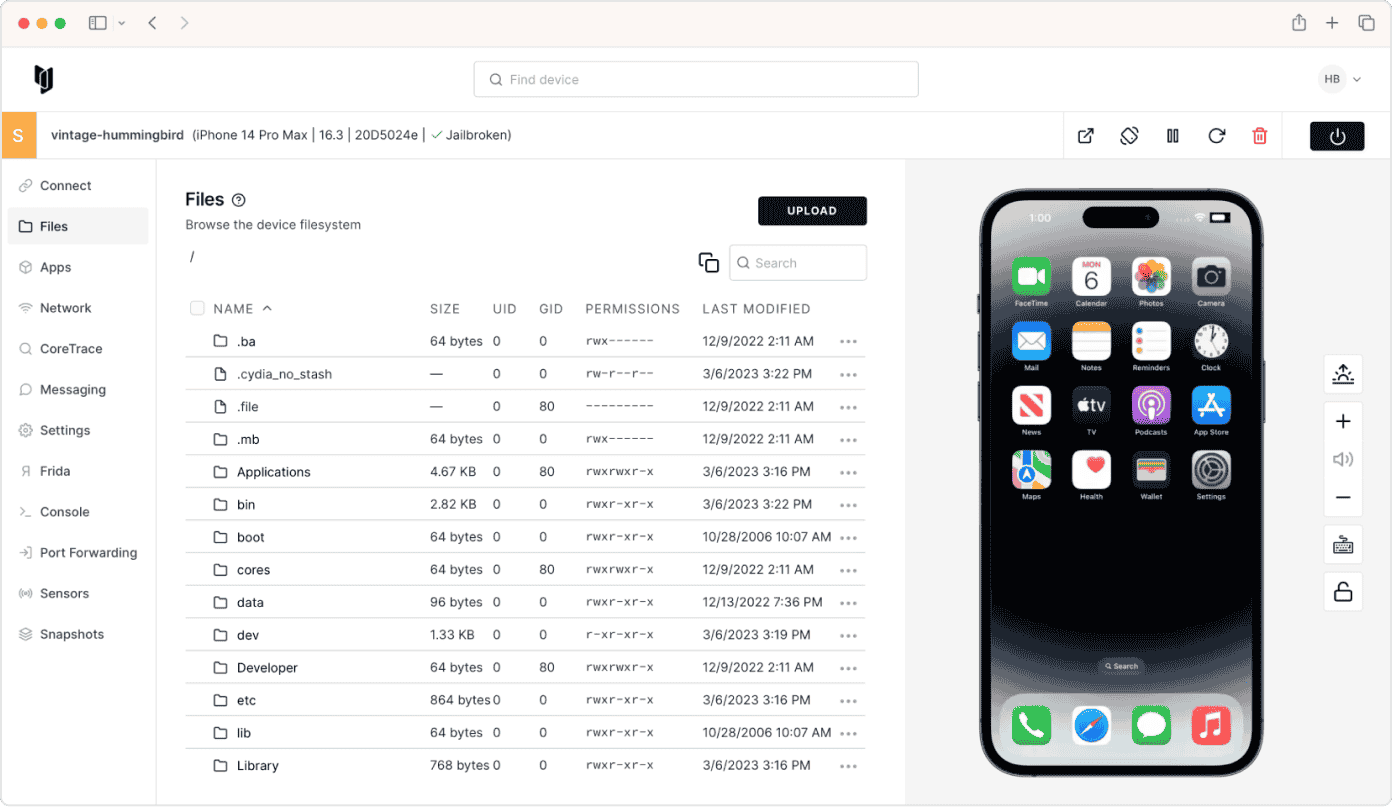
Corellium’s mobile application security testing workshop is built for professional pentesters ready to elevate their craft. This hands-on session puts you in the driver’s seat with Corellium’s virtual device platform, giving you the tools to dissect iOS and Android apps with precision. You’ll tackle real-world challenges—static and dynamic analysis, real-time network traffic inspection, jailbreak detection bypass, and automated security assessments—using a setup that cuts through the noise and gets to the vulnerabilities fast.
Seats are limited.
Headline about the Sponsors





Who Should Attend?
Designed for penetration testers, security researchers, red and blue team members and mobile developers who thrive on exposing exploitable flaws, this workshop delivers practical, high-impact techniques. You’ll leave equipped to handle the common mobile app security challenges, from identifying insecure data storage to manipulating runtime behavior on demand.
Registration
Secure your spot now for our FREE upcoming workshop on APRIL 24 (2pm-5pm)
Seats are limited
Registration is subject to approval
Register now for our free workshop
Key Learning Objectives
By the end of the workshop, you will have learned:
Test Environment Configuration: Choose from a range of hardware options & iOS firmware versions to configure your test environment, slashing administrative overhead and costs while maximizing your time on what matters—breaking stuff.
Data at Rest Exploitation: Pinpoint insecure storage issues—hardcoded credentials, keychain/keystore exposures—and leverage the Objection framework to dynamically probe and manipulate app data.
Data in Transit Domination: Dig into network traffic with real-time analysis to expose misconfigurations and weaknesses, no stone left unturned.
Reverse Engineering & Runtime Control: Tear apps apart, sidestep jailbreak detection, and exploit common attack vectors with exacting precision.
Automated MAST: Save time on repetitive tasks by using Corellium MATRIX to scan your app.
Integration with our SDK: Catch vulnerabilities earlier in the software lifecycle, before they turn into breaches, by integrating tests into your CI/CD system.
Tools Used
-
Corellium Cafe:
-
VPN Client
-
Mac OS – Viscosity or Tunnelblick
-
Windows – Viscosity
-
Linux – OpenVPN (sudo apt install openvpn)
-
-
Frida: https://frida.re/docs/home/
-
Objection: https://github.com/sensepost/objection
-
DB Browser for SQLite (or other SQLite viewer): https://sqlitebrowser.org/
Hardware Requirements
Participants will require a laptop with at least 8GB of RAM running a modern 64bit OS, with at least 20GB of free space after installing dependencies from the Tools Used section.
NOTE: Please bring your laptop’s charger.
